How do you select the best-distributed ledger technology for your business
Table of Contents
“Passion is energy. Feel the power that comes from focusing on what excites you.”
Oprah Winfrey (Ellevate, 2019)
Each one of us has unique interests, determining who we are and how we shall live our lives in the days to come. However, very few amongst us have the privilege to follow our aspirations.
Life, riddled with uncertainty, instils fear in the hearts and doubt in the minds of all prospective entrepreneurs and businessmen.
This combination of fear and self-doubt diverts many onto a path chosen by others around them, leaving only a handful hell-bent on carving their own way forward.

Fig. 1. The Iceberg Illusion (Lawrence, 2015).
However, true success can only be found by those who do not quit pursuing their objectives despite the magnitude of hardships or difficulties that stand in the way. Those who do not stop learning, excel at adapting, and embrace their failures with open arms, vowing never to REPEAT THEM, have the best chance to overcome the odds (see Fig. 1).
Nevertheless, most people lack the gritty attitude necessary to follow up on their vision, consequentially resulting in the gradual demise of their ambitions. As Tim Notke, a veteran basketball coach puts it (Irvine, 2016):
“Hard work beats talent when talent does not work hard”
The Realm of Business and Technology
In the realm of business, and especially in the case of adoption of novel technologies to empower the capabilities of a business, the most important thing to consider is that the goal, and the tool used to achieve that goal, should appeal to you on every level – RIGHT AWAY!
It should titillate the very essence of your being and SHOULD keep you awake at night, lost in deep thought rather than in deep slumber. This is necessary for excellence to be imbued in not only your work but also in your character.
The second thing AND THE MOST IMPORTANT factor is value addition.
Any type of business is a failure waiting to happen if it is not able to facilitate or be of service to HUMANKIND in any shape or form. The more wellbeing-inducive a service or product is, the steeper the value is going to be.
However, it is also equally important that an entrepreneur is never disheartened by challenges. Operating an SME, and being responsible for catalysing its success is indeed an extremely arduous task.
Great ideas are bound to be ignored during the initial stages, dismissed in the later stages, and rapidly mimicked or modified after becoming a certified success story.

How do you like me now?
Medium and Methodology
This leads us the third step – choosing a medium and the methodology of the intervention/project/ business that you believe can become a SUCCESS STORY, regardless of the discipline, multidiscipline, or trans-discipline being targeted.
Moreover, to ensure survival in the era of Information, you need to digitise this PASSION of yours into a practical, measurable, result-oriented, and scalable service/s or product/s. No matter what the short-term objectives are, the most important goal has to be either the TRANSITIONING or the TRANSFORMATION towards being a Digital Enterprise!
Medium
Nonetheless, the current medium (Internet) is riddled with vulnerabilities. Let me illustrate what I mean by vulnerabilities by way of a figure (see Fig. 2)
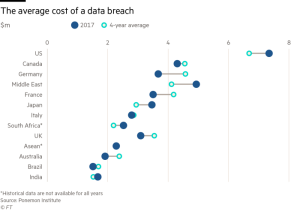
Fig. 2. The average cost of a data breach in $/millions (Kuchler, 2017).
You see, the Internet is really not a safe place at all. It is far from it because cybersecurity was the last thing engineers (i.e. Vint Cert and Bob Kahn) were concerned about when laying down its foundations.
They just wanted to make a command center that was indestructible (i.e. reassembled spontaneously), even in the wake of a nuclear attack.
In accordance with the directives of this project (called ARPANET), a distributed network of nodes was made that could specifically perform this FUNCTION. The builders were not concerned about some crazy delinquent trying to subvert the system from within as only a few scientists and engineers initially constituted the internet.
Still, the coming of world wide web instigated a vast majority of both public and private companies to come running into the fold of the logical dominion (i.e. Internet), rendering themselves equally susceptible to its dark side as well (See Fig. 2).
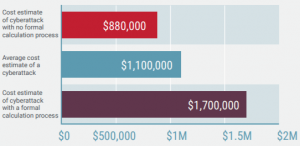
Fig. 3. Cost of a cyber-attack for a business with formal or informal calculation processes (Seals, 2019).
The Dot Com Drama
These businesses ushered in the Dot Com Era, as well as the Dot Com Bubble a few years later, due to the overvaluation of the benefits companies on the Internet could actually bring in 2001. Communication protocols were being formulated; the cost of energy production and storage was sky high; computer performance and size was highly impractical for the realisation of intricate tasks.
Even in those seemingly archaic times, it was not as if cybersecurity was never given the attention it deserved. In actuality, the problem was forced into the limelight but even then, was simply ignored or passed off as nonsense by “politicians”.
In 1998, a group of hackers under the alias LOpht gathered in front of a panel of US senators to declare:
“Your computers are not safe, not the software, not the hardware, not the networks that link them together. The companies that build these things don’t care, and they have no reason to care because failure costs them nothing. And the federal government has neither the skill nor the will to do anything about it”
Peiter C. Zatko aka Mudge (Timberg, 2015, par. 2)

Fig. 4. The team members of LOpht in front of Capitol Hill’s most powerful lawmakers: Fred D. Thompson, Joseph I. Lieberman, and John Glen (Luconi, 2018).
Fear, Innovation, Banking, and FinTech
Yet, little action resulted from the speech of LOpht’s leading member. As the market crashed and millions of Internet-based companies went bankrupt in the aftermath of the ’01 dot com bubble, smartphones and colossal web properties (i.e. Facebook) rose from the ashes like a phoenix to bring the internet back into the limelight again.
This time around, companies, especially the banks were very careful. Funding was rarely issued to the technology sector, however, that did not stop the industry from prospering.
Actually, it forced technologists to be even more innovative. Incubators and accelerators funded by the government or through the private sector emerged. E-commerce, social media, and digital advertisements led problem solvers onto crowd sharing platforms and in search of viable, instantaneous MICROTRANSACTIONS. Marketing strategies hybridised with computer science and disciplines such as finance, construction, real estate to introduce FinTech, ConTech, and PropTech respectively, driven more by new comers on the scene.
In comparison, banking practices witnessed limited innovation since the housing market crash. After 08’, It was this distrust that drove banks, once a leader in the space of innovation and technology, into taking a back seat with the other traditionalists.
Technologies of Trust – The Advent of Distributed Ledger Technology (DLT)
Nonetheless, computer science, in tandem with a myriad of disciplines, continued its march onwards – becoming better, faster, cheaper, and more systemised. A Start-up Culture dawned upon mankind whereby few people could challenge entire conglomerates provided that they were determined, passionate, and sufficiently capable.
Whilst many solutions have been introduced by this start-up movement, a key and hopefully revolutionary branch of technology came into being in 2008. It was termed as the most powerful “technology of trust” in the history of mankind (Goldman Sachs, 2019, par. 1). This was called:
Distributed Ledger Technologies
A contrivance made specifically to induce trust in a trustless environment.
Having a thorough understanding of DLTs, particularly what they are all about and why they came into existence, is of the utmost importance, especially when everyone claims that their platform is the best one to get the job done for YOU and YOUR BUSINESS.
The first DLT was originally made to introduce Bitcoin – a cryptocurrency having proof of work system (i.e. runs on Blockchain) that was introduced as a cryptographically secured digital alternative to the most predominant of all Fiat currencies – the US Dollar.
Why was cryptography necessary, you ask?
Have a look!!!

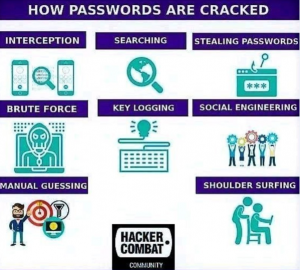
Wait let me guess? Is your password … (Hackers Combat Community, 2019)
Decentralisation Versus Centralisation
As evident from the Figure above, cryptography was necessary to ensure secure storage and communication over the computer network. However, it was not cryptography alone that propelled the rise of blockchain – IT WAS DECENTRALISATION.
Decentralisation made efficient through a technological modality that achieved a finality of consensus is a very unique and novel concept, quite analogous to the notion of properties with absolute inherent liquidity.
It was efficiency that not only forced business but whole empires, dating back to the medieval ages, to adopt the centralised approach in order to conduct the day to day operations under the umbrella of a well-established pyramidal hierarchy.
The centralisation of the digital plane came into being when huge web properties (i.e. Amazon, Facebook, Google, Yahoo, etc) garnered attention from the global community, catalysed by the onset and evolution of the smartphone embedded with a plethora of sensors.
Open protocols of the Internet were outpaced by these soon to be conglomerates, leading users to seamlessly adopt:
“Sophisticated, Centralised Services”
(Dixon, 2018, par. 2)

However, there were cons associated with the service as well. The centralisation of services made it extremely hard for start-ups, to grow their presence on the internet as major platforms governed the rules of the digital realm. It also created issues pertaining to fake news, algorithmic biases, EU privacy laws being breached and State sponsored bots. These issues will keep on incurring debate for a long time; however, distributed technologies do currently offer a way to overcome that.
But, rather than focussing on assimilation, many DLTs are competing amongst one another to be at the frontier of the third era of the internet – Web 3.0, in one way or the other.
Methodology
This is why structuring the methodology side of your DLT – based business is important. Each distributed ledger technology is different in terms of the methodology offered to make decentralisation efficacious. This is justifiable by the varying levels of applications, diverse trends, and dissimilar approaches that have been conceived in this space as of yet.
Initially, it is always better to view things holistically and therefore the distributed ledger technologies are explained in accordance with the generations they belong to in the paragraphs below.
First Generation of DLTs
The first generation marks the use of a proof of work system, Blockchain, in safely and immutably storing and exchanging a digital asset called Bitcoin. The term “Proof of Work” indicates the type of methodology used to achieve CONSENSUS in a network. A miner validates the transactions by solving extremely hard mathematical equations, making the entire network slow. Due to which, security is attained but at the cost of speed.
The disadvantages to this type of ledger are many, such as transactions requiring a long time, no finality of consensus, elicitation of a lot of computational power and unreliable updating procedures.
Second Generation of DLTs
The second generation was conceived when assets other than currencies were stored on these distributed ledgers. Thereafter, utility tokens emerged wherein goods and services were traded often in exchange for cryptocurrencies via DLTs. Although many second-generation platforms have not been able to curtail the nascent level challenges, nevertheless, the technology proved to be useful (particularly due to the ICO craze – which is a debate in its own right re the benefits and drawbacks associated with ICOs) that even banks started reverting back to researching and incorporating innovative FinTech solutions. This also happened to be the generation that introduced permissioned ledger for the first time as Bitcoin was open to all (i.e. the public being a permission-less ledger).
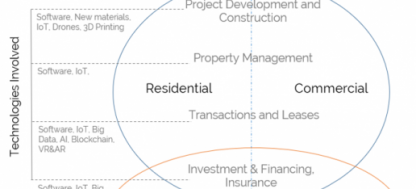
Confused as to what these terminologies are actually referring to?
The difference is outlined in the image below
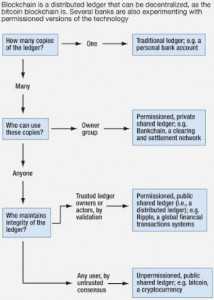
Third Generation of DLTs
The third generation marked the entry of smart contracts, whereby all the agreements between multiple parties that engaged in the exchange of services was codified in a manner that imbued efficiency within the decentralised system – in order to validate transactions.
Ethereum invested heavily into this, creating the EVM (Ethereum Virtual Machine) to power a system based upon the proof of stake of the participating node. Stakes were involved and deemed as collateral if goals previously set between the investor and business owner or between client and service provider/ manufacturer were not achieved. Exemplary DLTs of this generation are IOTA, Nano, and Cardano.
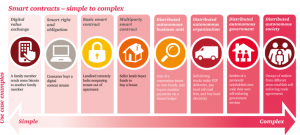
Types of smart contracts rising up the complexity scale (Morrison, 2016)
To execute the most complex of all smart contracts and process them countless times per second requires a platform to have high throughput capability; quick and transparent consensus; positive correlation with microtransactions and FAIRNESS – a key ingredient missing in the third generation.
Fourth Generation of DLTs
Therefore, at this point in time, the only viable 4th generation DLT, in terms of capabilities of the underlying protocol, is Hashgraph (i.e. Gossip about Gossip over Virtual Voting). Still, that too awaits its open access, as much shall be determined after that.
Post – Scriptum
Whatever generation you may choose, remember that the entire DLT technology is currently at its formative stages. There are many platforms that are offering high throughput, short term relevance, and ease of access. But the success of your business is also dependent upon the way you envision your legacy. Whether you specifically target a smart contract of higher complexity or prefer scaling up from simpler ones – do remember that the need of DLTs did not arise due to the need of decentralisation alone but for decentralising to be done securely and surely.
Another major boom awaits us and the only difference this time around is that more people value mathematically proven cybersecurity to empower their business. Therefore, my final recommendation with regards to choosing the best DLT for your business is to ask for proofs; especially regarding the finality of consensus and the level of security provided.
Finality of Consensus
Most DLTs (i.e. blockchains) are reliant on forking to collectively agree on an update. The more electronic devices (nodes) that run on the network, the more secure the network gets. However, one needs to be wary of the hard forks that are able to change the fundamentals of deriving consensus. This leads to splits and divergence in the entire network, as seen on Ethereum this year and Bitcoin variations in previous years.
However, it cannot be denied that each DLT has contributed in some way or the other in the development of the discipline and currently, we are finally witnessing the merger of ideas and technologies where the best elements of each DLT are being made interoperable with one another to derive a well-rounded service. That needs to happen more. A lot more and I reckon it surely will.
Level of Security
Yet, there still remains a blatant issue of security. Security of computer network is gauged in accordance with Byzantine Fault Tolerance. The gold standard amongst all Byzantine Fault Tolerance thresholds necessitates that if someone is able to influence or fork away 33% of your nodes that constitute the network of your business, your system has been compromised – GAME OVER! While difficult, it is not impossible.
So far, only one DLT has been able to prove its ABFT nature. It promises that if your business is “legally” designed in a manner where the best amongst all shreds of evidence dictate your actions and deliberate contingencies are established well beforehand, you will be able to retain the control of 66% of your hashing power through this technology. This is the fourth generation DLT, Hashgraph.
But, as discussed, it too needs to attain considerable numbers to fulfil the potential of its patented technology.
Conclusion
In the end, I would like to point out that your choice of DLT is a personification of your business needs, acumen, and understanding. The bigger and more mission-critical your objectives are, the more risk aversive you shall need to be. Therefore, start inducing trust where you find it lacking and use the best modalities at your disposal to solve the problems you see around yourself.
With my ventures like Zisk Properties and SeerBytes, we yearn to scale all the limits known to man – setting our sights to achieve the impossible, the unknown, and to venture beyond to truly display the beauty of interoperability through technologically augmented property investments.
To follow our example, you would need to attract and incentivise the best and the most relevant knowledge workers you can find that can systemise operations that have never been tried before. I invite you all to explore such technological prospects with me and my team.
References
Dixon, C. (2018, February 18). Why Decentralization Matters.
Ellevate. (2019). Passion.
Goldman Sachs. (2019). Blockchain – The New Technology of Trust.
Hackers Combat Community. (2019). Home Page.
Irvene, D. (2016, May 18). Forget Talent, Focus on Hard work.
Kuchler, H. (2017, November 8). Cost of Cybercrime Rises Rapidly as Attacks Increase.
Lawrence, T. (2015, December 18). How Success is the Result of Hard Work.
Luconi, C. (2018, August 16). On Being A Pioneer – Lessons Learned from The LOpht.
Seals, T. (2019, January 15). $1.7M is the Average Cost of a Cyber Attack.
Timberg, C. (2015, June 22). A Disaster Foretold – And Ignored.

 5245
5245
 5245
5245

 5245
5245
 5245
5245

 5245
5245
 5245
5245

 5245
5245
 5245
5245

 5245
5245
 5245
5245

 5245
5245
 5245
5245